While the vast majority of websites are built with PHP as their core programming language (including of course all the PHP frameworks and leading PHP based CMS platforms like WordPress), the Website Security is a continuously aching concern across websites. It is also one of the most neglected aspects across most websites built with PHP.
How to fix the security issues in PHP websites? Are there some time-tested ways to deal with security threats and vulnerabilities and prevent PHP websites from being hacked? Well, based on the experience of many webmasters and the security protocols that really worked well for websites, here we are going to explain the key ways to boost security and make the site hacking-proof. It is needless to say PHP Development Services should take a note of these security solutions.
1. Take Guard Against SQL Injection
SQL Injection is one of the commonest hacking mechanisms that most websites are not fully equipped to deal with. This is the only technique that can easily bypass the authentication measures or to manipulate the login data of a user.
This is how the login credential is checked for authenticating the user inputs in the respective fields:
$uname=$_REQUEST[‘username’];
$pass=$_REQUEST[‘password’];
$mysql_query(“select * from users where username='”.$uname.” and password='”.$pass.”‘”);
Now, in an unusual scenario instead of entering the username and password if someone enters a value like the following, it looks like this.
In such case, the user query will be like this:
Username=’ or ‘1’=’1
Password= ‘ or ‘1’=’1
In such case, the user query will be like this:
1
select * from users where username=” OR ‘1’=’1′ and password=” OR ‘1’=’1′
The trick works very simply based on the similar value. The value of input ‘1’ is always equal to ‘1’ and hence the query generated by the hacker will easily be authenticated as true and thus the authentication process can be bypassed.
Question is how to prevent such bypassing of login credentials? This requires usingmysqli_real_escape_string to safeguard the query from such injections. After using this protective code it will look like the following:
<?php
$uname= mysqli_real_escape_string($_REQUEST[‘username’]);//to secure PHP websites from hackers
$pass= mysqli_real_escape_string($_REQUEST[‘password’]);//to secure PHP websites from hackers
$mysql_query(“select * from users where username='”.$uname.” and password='”.$pass.”‘”);
The above-mentioned method is already a proven way to safeguard your PHP website from the hacker’s intrusions.
2. Keep Software Up To Date
This may look like a preposterous advice but considering the importance of using updated software for security reasons it deserves a mention here. You should always use the latest versions of the operating systems and all the third party plugins, software, and CMS to keep your website secure. This is mainly because, an outdated software or application is more vulnerable to security threats, malicious programs, and hacking activities.
This is particularly crucial if you are using a self-hosted solution. A reputed managed hosting service is generally safer as such services keep themselves always updated with latest OS and software versions.
If you are using a managed hosting solution then you don’t need to worry so much about applying security updates for the operating system as the hosting company should take care of this. When your CMS website notify you of available system updates, instead of ignoring them avail the updates and keep your website up to date.
Apart from following the best practices as mentioned above you can also take help of effective developer tools such as npm, Composer and RubyGems evaluate the dependencies on software applications and for tracking the security vulnerabilities.
Read More: 7 Top WordPress Security Tips And Tricks To Defy Website Hacking
3. Check Session In Every Protected Page
Checking the sessions of the user is another crucial security task to prevent threats. After each successful user login, you need to check the user’s session in every page marked as protected. This requires including the respective files for checking user session in every protected page.
4. Always Use .php As An Extension
While using PHP for the codebase of your website, it is the established protocol to use the .php extension with every file. This actually prevents anyone from accessing the source code of the functions with extensions like .inc, or .ini over the web. To protect your source code from unauthorized access over the web only .php extensions.
5. Input Validation
source:dribbble.com
There are too many PHP websites that still depend on client side programs for validating inputs. Client-side programs like JavaScript-based input validation programs can easily be bypassed. You need to use rather server-side input validation programs that cannot be bypassed.
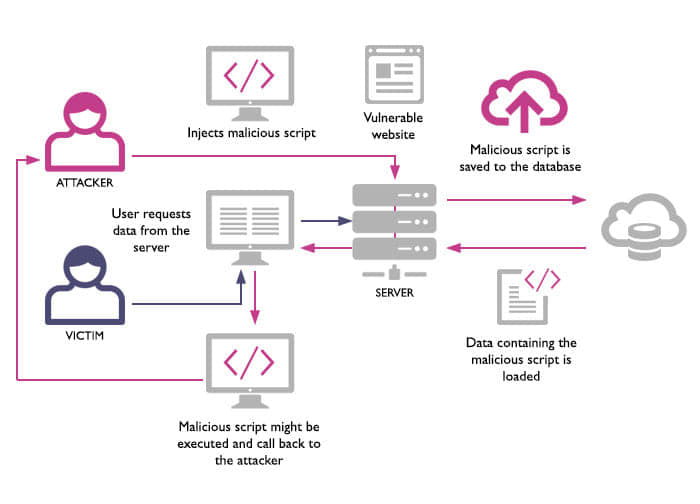
6. Protect Against XSS Attacks
Cross-site scripting (XSS) is one of the commonest methods of hacking a website by injecting JavaScript into the web pages. Such malicious programs can do permanent harm to your website. Through such malicious programs, your website content can be changed or stolen. Usually, these programs run on the browsers used by the users and interfere with the user experience.
source:res.cloudinary.com
Cross-site scripting mainly happens through malicious program links posted through comments and other user-generated contents. Though by using advanced frameworks like AngularJS and EmberJS equipped with protection from cross-site scripting is a great way to prevent such intrusions, you should also prevent mixing of client side and server side rendering to reduce malicious JavaScript injections.
There is another very effective way to prevent XSS attacks. Content Security Policy (CSP) which works like a server-side header to direct browser about the JavaScript execution on any given page, can be a really powerful tool to prevent cross-site scripting attacks.
7. Check Your Passwords
source:dribbble.com
Though it has always been subjecting of discussion and using strong passwords has always been a basic security requirement, many web admins simply do not do this. This is why we are going to explain some effective password practices to prevent security breaches.
- The standard practice is to use at least 8 character passwords that include a number and a mix of upper and lower case letters.
- Passwords can be more protected by storing the same as encrypted values. Use some quality hashing algorithms for this.
- In case your password for admin area is still being accessed or guessed, use hashed passwords as they cannot be decrypted.
8. Use HTTPS Protocol
HTTPS is a trusted protocol to boost security to a website domain. This protocol basically prevents any alteration, interception of the contents users are using when talking to the server for accessing a website.
This not only prevents intrusions of all types but also protects the private and confidential information of the users. Any website dealing with confidential user information such as financial and billing data must use HTTPS to safeguard data from intrusions.
Furthermore, if you are already using HTTPS, you can boost security settings better by opting for HTTP Strict Transport Security (HSTS). This basically works like a header and directs the server to block any vulnerable HTTP request for the whole website.
9. Use The Following Security Tools
When you finally consider having done everything to boost your website security by following the above-mentioned practices and principles, it is time to test your website security. The developers can take help of an array of quality tools for this. These tools just by mimicking the hacking activities as mentioned earlier test the preventive and security mechanism of the website.
Let us list some free and reliable testing tools.
- Netsparker is both available in free and trial version and good for testing XSS attacks as well as SQL injection.
- OpenVAS is a free and open source security testing tool with many advanced features.
- SecurityHeaders.io allows free security and configuration checks for your website.
- Xenotix XSS Exploit Framework is another great tool specialized in preventing XSS attacks. It is equipped with a large number of XSS attack examples.
Do not depend completely on automated testing as automated tests often do not detect all the security vulnerabilities. Always give priority to solving the critical security issues as they can lead to hacking events.
10. Stay Away From File Uploads
Security breaches are way common today and permitting users to upload files is another harmful endeavor for your website security. Letting the users to upload files can be dangerous, even if it’s about changing the display picture. Wondering how a simple file can be a major impact to the security concerns?
Well, the file uploaded whether it is a .jpg file or any .php file may contain a script which when uploaded on the server will completely unlock the essential information of your website. In case a file is uploaded, you need to take care of it with great suspicion. Moreover, don’t commit the mistake of assuming the file type based on the file extension. As this can be easily faked.
When you open such fake extension files to check the functions and ensure if the image size is foolproof or not, you may fall in trouble. As there’s a comment section that may contain PHP code and can be easily implemented on the server. So precautions should be taken?
From the above discussion, can we guess that the essential point is to stop users from being able to implement any kind of file they upload? Web servers have a default setting of not executing the files that have .jpg or .png extension, however, we cannot completely trust that the file is an image file only. As the file name with image.jpp.php can easily be uploaded.
One solution is to rename the file while uploading to guarantee about the file extension or alter the file permission, like chmod 0666 to stop the execution of the file. In case you are using *nix, you can generate a .htaccess file which will just enable access to set files not allowing the double extension attack.
deny from all
<Files ~ “^\w+\.(gif|jpe?g|png)$”>
order deny, allow
allow from all
</Files>
That means, the most acclaimed option is to stop the direct access of the uploaded files altogether. In this way, the number of files that are uploaded on your website will be stored in a folder which can be accessed outside the webroot or in a database as a blob. When your files are not accessible, you need to write a script that will fetch all the files from a private folder and send you to the browser. Along with that, remember the image tags support an src attribute which is not a direct URL to an image, that means the src attribute can address to your file delivery script enabling you to set the required content type in the HTTP header. For instance:
<img src=”/imageDelivery.php?id=1234″ />
<?php
// imageDelivery.php
// Fetch image filename from database based on $_GET[“id”]
…
// Deliver image to browser
Header(‘Content-Type: image/gif’);
readfile(‘images/’.$fileName);
?>
Usually, the hosting service providers help you with the server configuration, but in case you are managing the hosting for your own website on your own server, you need to ensure the following things.
- Make sure your server has a firewall setup and has the capability to block all non-essential ports
- Set up a DMZ (Demilitarized Zone) that enables access to port 80 and 443 from the outside the world. This may be impossible when you don’t have the access to your server from the internal network because for this you will require to open up ports for file uploading and remote access over SSH or RDP.
- When you are uploading files from the Internet, ensure you use a secure transport method like SFTP or SSH.
- If possible you adopt different server for database and website. With this endeavor, you ensure that the database server won’t be accessed directly and only your web server can access it. So you will diminish the potential of your data being exposed.
Moreover, remember to restrict the physical access of your server.
Security threats are now more sophisticated than ever before. Naturally, you cannot just depend on outdated security practices. If you want to prevent your PHP website from hacking, have a comprehensive strategy with all the best practices and principles as explained above.
Do you want to hire PHP developers with proven expertise on the above-mentioned security practices and tools? CMARIX as one of the leading web development services can take care of all your potential web security concerns.