Securing these workloads has become a significant priority as more and more companies choose the cloud as the target platform for their business-critical workloads. Improving your organization’s cyber hygiene starts with developing a clear risk management plan that addresses the application layer, cloud-specific security policies, Azure AI services, and infrastructure as a whole. The native security tools available on the Azure platform are a fantastic place to start if you are running workloads on it.
But as your business and cloud workloads grow, you’ll also want to add an extra security layer using reliable third-party solutions. Let’s understand the different types of security tools in Azure in our next section.
10 Azure Security Tools and Features to Protect Your Business
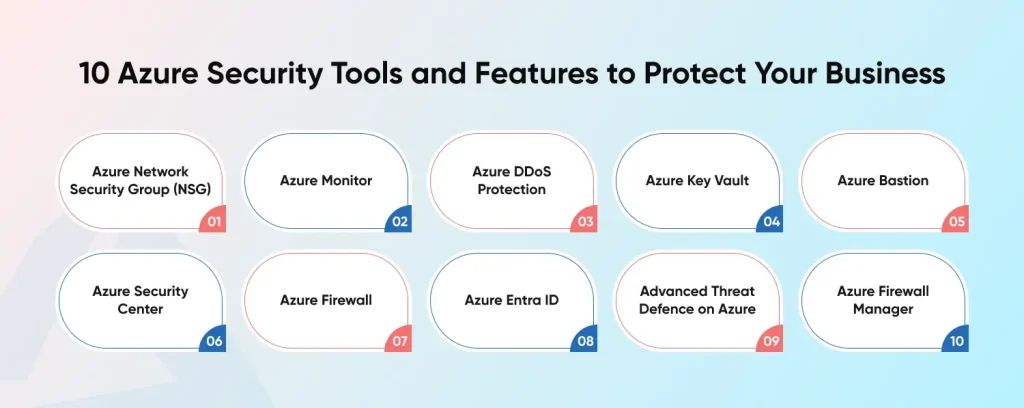
1. Azure Network Security Group (NSG): Customising Network Traffic
Azure Virtual Networks’ network traffic is vitally protected by Azure Network Security Groups (NSGs). They act as programmable gatekeepers, letting users establish certain guidelines for the flow of traffic into and out of Azure Resources. Consider them as traffic controllers; by controlling which connections are permitted and prohibited, they provide a safe and well-managed network environment.
Azure Network Security Group’s (NSG) Features:
- Establish rules for traffic blocking according to protocol, port, and source and destination IP addresses.
- prevents unwanted access and shields resources from harmful traffic.
- centrally administers security policy across many resources.
- specifies detailed guidelines for controlling both inbound and outbound traffic.
- As your network expands, you may quickly apply NSGs to new resources.
2. Azure Monitor: Constant Health Insights for Resources
Another crucial component of cloud security tools is Azure Monitor. It collects, examines, and reacts to information about your apps and services from your servers and the cloud to guarantee they remain operational. It provides information about the performance of your apps and assists in identifying and resolving issues before they become problematic.
Important Azure Monitor Features:
- Tailored monitoring experiences are provided via simplified monitoring tools.
- Observing ingested data is made possible by comprehensive data visualization.
3. Azure DDoS Protection for Denial-of-Service Attacks
Azure DDoS Protection distinguishes between legitimate traffic and possible assaults by adjusting its configurations based on your typical traffic patterns. Microsoft Azure effectively counters even the most complex assaults by utilizing its global infrastructure and providing complete information through tools like attack logs, alerts, and real-time monitoring with Azure security monitoring tools. Azure DDoS Protection offers flexible solutions suitable for all types of enterprises, whether you want to protect certain web destinations or your entire virtual network.
Essential Elements of Azure DDoS Defence:
- Adaptive threat intelligence is used to block sophisticated DDoS attacks automatically.
- Eliminates harmful traffic at the network’s edge, lessening its influence on applications.
- Provide thorough insights into DDoS attacks so that action can be taken quickly.
- Quickly deploys to protect all resources upon activation, decreasing latency and application downtime in the event of an attack.
4. Safeguarding Your Azure Secrets with Azure Key Vault
A cloud-native solution called Azure Key Vault is made to safely handle and store private data, including cryptographic keys, passwords, certificates, and API credentials. Vaults and controlled hardware security module (HSM) pools are its two main constituents. Software and HSM-protected keys, secrets, and certificates are stored in vaults; only HSM-secured keys are stored in controlled HSM pools.
Important Azure Key Vault Features:
- Effectively safeguards cryptographic keys, certificates, passwords, and API keys.
- It maintains HSM pools exclusively for HSM-backed keys and supports software and HSM-backed key vaults.
- Enables vault owners to establish vaults, manage vital lifecycles, set auditing, and regulate access.
- Designates particular positions, such as Managed HSM Administrators, Crypto Officers/Users, Vault Owners, and Vault Consumers.

5. Azure Bastion: Safe Virtual Machine Access Point
A notable option among the several Azure cloud security options is Azure Bastion. Without exposing them to the Internet, it makes virtual machine access safer and simpler. Depending on what your business needs and can afford, you, as a single user or large organization, have a variety of options to select from.
Important Azure Bastion Features:
- There is no need for extra software or agents on virtual machines (VMs) or browsers because Azure Portal or a native client offers single-click access to RDP and SSH connections.
- Maintaining seamless interoperability with current firewalls and security perimeters is ensured by integrating a contemporary HTML5-based web client with standard TLS ports.
- The Bastion Standard permits the administration of several concurrent SSH and RDP connections.
- With a single protected access point (Bastion host), you can reach every virtual machine in a local or peer virtual network using private IP addresses instead of public ones on the VMs.
6. Azure Security Center: Your Central Security Hub
Enhancing and monitoring security across IT environments, from on-premises setups to Azure and other cloud platforms, is the primary function of Azure Security Centre, one of the key components of the Microsoft Azure security tools list. It functions as your cloud environment’s protector. It monitors everything that takes place there, including attempts to access your data and any questionable activity. In addition, it assists you in identifying and resolving security flaws before they become major issues, guaranteeing the security of your cloud.
Azure Security Center’s Salient Features:
- Agent deployment for security state monitoring and problem identification on virtual computers.
- Finding systems with out-of-date anti-malware software, outdated OS configurations, and update gaps is all part of security status monitoring.
- Recognizing the security posture of applications, data, storage, networks, and access restrictions.
- Unique security policy configuration for each subscription to preserve security configurations.
- Capability for automated responses based on Playbooks developed on Azure Logic Apps.
7. Safeguarding Your Virtual Network with Azure Firewall
A cloud-based security solution called Azure Firewall is made to protect the resources in your Azure Virtual Network. It keeps an eye on everything that goes on in your virtual area, much like a vigilant guard. This firewall can easily manage a large volume of traffic and is always up and running. It can be used to establish restrictions on what or who is allowed access to your networks and apps. Additionally, it keeps a thorough log of every action, so you know exactly what is going on. Elevate your cloud security strategy by utilizing the potent Azure security features.
Azure Firewall’s Principal Features:
- Get real-time notifications and prevent traffic to and from dangerous IP addresses and websites.
- A scalable and resilient cloud-native firewall can simplify deployment and management.
- To stop malware via encrypted connections, use TLS inspection.
- Unified rules should be use to centrally control security for all virtual networks.
- Get security alerts in real-time using Microsoft’s threat intelligence.
- For access to the Azure Virtual Network, make use of turnkey firewall controls.
8. Azure Entra ID: Safeguarding User Entry
One of the best Azure security solutions, Azure Entra ID (previously known as Azure Active Directory) is your virtual protector for your cloud assets. Controlling who has access to what resources is made easier by its centralize handling of user identities and access rights. Increasing protection against unwanted access attempts with the addition of security mechanisms like multifactor authentication strengthens overall security.
Azure Active Directory’s Salient Features:
- User access permissions are consolidated by Azure Entra ID, making resource management easier.
- By erecting a barrier, features like multifactor authentication improve security.
9. Advanced Threat Defence on Azure
A key component of Azure’s array of cloud security solutions is Azure Advanced Threat Protection (ATP). It’s more of a cloud service that continuously monitors domain controllers and analyses events to assist in safeguarding organizations from insider threats and compromised identities. It recognizes unusual activity both on-premises and in the cloud and notifies system administrators of it.
Azure Advanced Threat Protection’s Salient Features:
- Monitors user behavior and sends alerts for anomalous activity, such as unauthorized access to critical documents or strange login patterns.
- Reduces the possibility of compromised user accounts by offering security reports and analytics on user profiles. Lateral Movement vectors (LMPs) are use to visualize possible lateral attack vectors.
- Detects the stages of a cyberattack and breaches, such as data exfiltration, lateral movement, compromised credentials, and reconnaissance.
10. Streamlined Control for Your Firewall Defences with Azure Firewall Manager
One of the most important components of Azure cloud security solutions is Azure Firewall Manager, which simplifies security policies and routes for cloud-based security boundaries. Along with configuring Azure Firewalls, users may also manage Azure DDoS Protection plans and Azure Web Application Firewall (WAF) policies. To configure and manage many Azure Firewall instances across different regions and subscriptions, Firewall Manager offers a unified platform.
Important Azure Firewall Manager Features:
- A single control plane to manage instances of Azure Firewall.
- From a single, central location, effortlessly configure and manage several Azure Firewall instances across various regions and subscriptions.
- Oversee the configuration of security policies and logging for several Azure Firewall instances.
- For safe virtual hub installations and hub virtual networks, centralize Azure Firewall management.
Conclusion
Strong security measures must be put in place as cloud adoption picks up speed to protect sensitive data and uphold compliance. Azure’s security solutions offer a complete defense against dynamic threats for your cloud environment. But our Microsoft development services like Azure support a safe, legal, and effective cloud environment while also improving security posture.
Whether it’s controlling user access, safeguarding apps, or securing virtual networks, these tools enable your company to develop a strong, proactive defense plan. Build a serverless web app in Azure with CMARIX to improve security posture and promote a safe, legal, and effective cloud environment.
Frequently Asked Questions
How Does Azure Firewall Manager Help with Security?
Secured virtual hubs can be established with Azure Firewall Manager to protect cloud network traffic going to private IP addresses, Azure PaaS, and the Internet. The firewall has automated traffic routing, therefore user-defined routes (UDRs) are not necessary.
What Are Microsoft Azure Security Technologies?
A cloud workload protection system that offers superior threat protection and security management for hybrid cloud workloads. Microsoft Sentinel. A cloud-native, scalable system that provides threat intelligence and intelligent security analytics to the entire organization.
Is Azure Security in Demand?
The need for qualified experts in cloud security is rising. One of the top cloud platforms, Microsoft Azure, provides security solutions for companies. Gaining experience as a Microsoft Azure Security Engineer might lead to opportunities in this quickly expanding industry.
What Are the Different Options for Security in Azure?
Network settings are separated and secure thanks to distributed denial of service (DDoS) prevention, virtual networks, and network security groups (NSGs). Data is secure while it is in transit thanks to Microsoft Azure network security features, which also guard against unwanted network access.