Quick Summary: Customer data drives business, but CRM systems are prime targets for breaches and compliance risks. This guide provides CRM and data protection strategies, best practices, and expert insights to secure data, ensure regulatory compliance, and build customer trust.
Access to consumer data is the most valuable asset for most businesses in today’s digital age. Naturally, then customer relationship management systems serve as the central hub for such data, and are at the heart of modern business operations. Such systems hold valuable information about customers. Every aspect of their personal details, transaction logs, purchasing behaviour, and even individual preferences gets stored on these systems. Keeping CRM and data secure is not only a technical requirement, but also an important practice from an ethical, security, and reputation perspective.
To protect CRM data against data breaches, it is essential to follow data protection practices for CRMs, understand the four pillars of CRM cybersecurity, and implement GDPR compliant CRM systems. Today, we will cover all important aspects of CRM and data protection, as well as how to ensure the proper implementation of enterprise CRM solutions.
Understanding CRM Security: Data Privacy vs. Data Security
| Aspect | Data Privacy in CRM | Data Security in CRM |
| Purpose | Ensure ethical, lawful collection, processing, and sharing of consumer information. Protect user rights and comply with regulations. | Protect customer data from unauthorized access, breaches, and misuse using technical defenses. |
| Nature | Policy-driven, compliance-focused, emphasizing consent, transparency, and responsible use of data. | Technology-driven, focused on implementing defenses, monitoring systems, and data protection practices. |
| CRM and Data Protection Examples |
|
|
| Key Regulations | GDPR, CCPA, HIPAA, and other data protection laws that focus on how data is collected, used, and shared. | GDPR, NIST, ISO/IEC 27001 (for security frameworks), PCI-DSS (for payment data security), etc. |
| Focus Area | Consent, transparency, and respecting customer rights. | Protection of data through encryption, authentication, and real-time monitoring. |
| Common Challenges | Balancing data utility with respecting privacy rights. Managing complex consent preferences across various channels. | Ensuring that security protocols are up-to-date, preventing breaches, and responding quickly to potential security incidents. |
When combined, data privacy defines the ethical and legal framework of how data should be handled, while data security enforces the technical protections to keep it safe. This distinction is important because CRM systems can have robust security measures but still fail to comply with privacy regulations, or one that prioritizes privacy over security can still be vulnerable to breaches. Both need to work together to truly protect your CRM and data.
What are the Security Concerns of CRM?
To put things in perspective, and realising that these threats are more real than hypothetical, you should know that Allianz Life Insurance of North America experienced a major breach through a third-party cloud CRM. Attackers used social engineering to access the personal data of over 1.4 million customers. This demonstrates that CRM security risks are genuine and warrant serious consideration.
Let’s start with the basics. What are these security concerns that we should address? A CRM is more than a contact list; it holds customer data, purchase history, communication records, and even financial details. These risks usually fall into a few main categories: authentication is poorly managed, which can give outsiders/insiders more access than they should have.
- Data Breaches: Attackers can exploit your data in various ways, including phishing, misconfigured cloud storage, and vulnerabilities in third-party applications.
- Compliance Failures: One of the most common CRM data security concerns is the inability to keep up with regulatory requirements, such as GDPR and CCPA, which demand strict handling of personal data. Failure to comply, even if unintentional, can cause serious consequences.
- Integration Risks: CRMs are often part of a connected ecosystem that interacts with other business applications and software for marketing, billing, and customer service tools. Each integration point can be an entry point for attackers.
- Insider Threats: Unfortunately, this happens more often than you’d like to believe; employees or contractors with legitimate access can also misuse data, whether accidentally or intentionally.
Why is CRM Data Security Important?
Financial Costs and Reputational Damage:
A security incident can result in major monetary loss. This includes fines, legal fees, and remediation efforts. The average cost of a data breach reached $4.88 million in 2024. Even if you agree and comply with everything promptly, customers are still likely to lose trust in businesses that can’t protect customer data, which can result in a decline in future business.
Legal and Regulatory Compliance:
Naturally, governments of all countries have also established rules and regulations to protect their consumer data. Failure to be a GDPR compliant CRM or comply with other frameworks, such as HIPAA and CCPA, can result in severe legal actions.
Operational Disruptions and Competitive Disadvantage:
Any breach in CRM or data security can disrupt business operations and force systems offline, stopping productivity. In competitive markets, companies with a strong reputation for CRM security often have an advantage over their competitors.

What are the Key Pillars for Robust CRM Cybersecurity?
Protecting CRM systems can’t be limited to fixing problems. It requires a clear and well-planned approach. Effective cybersecurity relies on having skilled CRM developers who focus on four key areas: workforce, strategy, process, and technology.
CRM Cybersecurity Pillar #1: Workforce
Employees are often both the strongest defense and the weakest link in security. That is why cultivating a security-first mindset across your team is crucial.
- Security Awareness Training: Regularly train all staff, not just developers, to recognize phishing attempts, social engineering tricks, and unsafe browsing habits.
- Role-Based Access Control (RBAC): Limit access so employees only see what they need to complete their jobs. This reduces the risk of an account being compromised.
- Passwords & MFA: Enforce strong, unique passwords and always require multi-factor authentication (MFA) for CRM logins.
- Incident Reporting Culture: Encourage employees to report suspicious activity promptly and without fear of retribution or blame. Quick reporting can prevent a minor issue from escalating into a major breach.
CRM Cybersecurity Pillar #2: Strategy
Cybersecurity is an ongoing cycle of planning, monitoring, and adapting to stay ahead of threats.
- Risk Assessments & Audits: Regularly test your CRM, networks, and workflows to uncover weak spots before attackers do.
- Data Minimization and Retention : Don’t collect data just because you can. Only gather what’s essential for your business, and have clear rules about how long you’ll keep it. Old, unnecessary data sitting in your CRM is just extra risk waiting to be exploited.
- Compliance and Regulations: Laws like GDPR and CCPA aren’t optional. They shape how you store, manage, and share customer information. Falling short here isn’t just about fines; it’s about trust. Customers want to know their data is handled with care.
- Vendor Due Diligence: If you’re using a CRM platform like Salesforce, Zoho, or HubSpot,their security standards are connected to theirs. Before committing, research their certifications, history of breaches, and published security practices.
CRM Cybersecurity Pillar #3: Process
Strong processes ensure consistency and fast responses when threats arise.
- Incident Response Plan: A breach is never the time to improvise. Having a step-by-step plan, including containment, investigation, and recovery, means your team can move quickly instead of panicking.
- Regular Data Backups and Recovery Testing: Backups are great, but they’re useless if you don’t know they work. Automate them and test your recovery so you can always stay on guard.
- Continuous Logging and Monitoring: Every login, data pull, and every unusual activity should leave a trace. Real-time monitoring helps you identify unusual behavior, such as repeated failed logins, before it escalates into a disaster.
- Change Management: Even minor adjustments to your CRM settings can lead to significant security vulnerabilities if not properly monitored. Document all changes, keep testing the system before and after rollout, and maintain a clear audit trail.
CRM Cybersecurity Pillar #4: Technology
The right tools strengthen defenses and keep threats at bay.
- Data Encryption: Encrypt sensitive CRM data both in transit and at rest to keep it unreadable if intercepted.
- Firewalls & Endpoint Security: Deploy firewalls, intrusion prevention systems, and endpoint detection and response tools to safeguard all devices accessing the CRM.
- Two-Factor Authentication: Add a proper layer of security using a 2FA or MFA authentication system, making it more difficult for exploiters to access accounts even if credentials are compromised.
- AI & Machine Learning: Deploy AI-driven tools to spot unusual activity, forecast risks, and accelerate threat response beyond human capabilities.
A Step-by-Step Guide to Securing Your CRM System
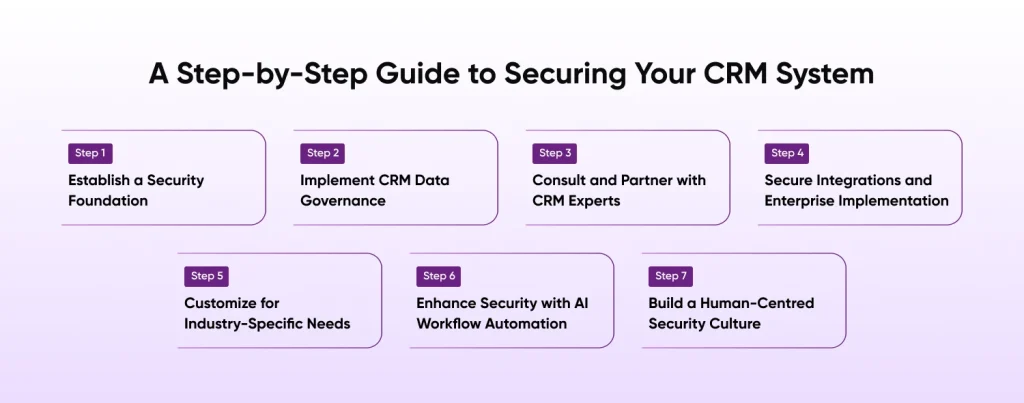
Protecting sensitive customer information is not a one-time task that can be ticked off a to-do list. It is a structured process that combines technology, governance, and expertise to achieve its objectives. Here is a logical flow of data protection practices for CRMs that organizations can adopt to achieve stronger CRM in cybersecurity and compliance.
Step 1: Establish a Security Foundation
Start with the basics and fundamentals by enforcing encryption for all customer records. Next, ask your team to set up role-based access controls, strong authentication measures, and multi-factor logins. Implementing these measures will help ensure CRM data security at its core and meet all the requirements of the Data Protection Act, as well as the CRM system’s requirements.
Step 2: Implement CRM Data Governance
Define clear rules on how the data will be collected, retained, and disposed of. CRM data governance is crucial for the ethical and compliant management of sensitive information while reducing the risk of unnecessary exposure. By following proper CRM and data protection examples, businesses can prevent data sprawling and reduce risks.
Step 3: Consult and Partner with CRM Experts
It is better not to take a DIY approach to CRM security; it should be handled by experienced professionals. Collaborate with experts who have successfully implemented secure CRM systems across various industries. Hire dedicated CRM developers or work with a trusted software development services company.
Step 4: Secure Integrations and Enterprise Implementation
As CRMs interact with marketing, billing, and support tools, CRM integrations open up numerous potential exploitation points. When planning a high-level CRM integration for SaaS businesses or the implementation of enterprise CRM solutions, adopt secure APIs, perform regular testing, and maintain audit logs to reduce vulnerabilities.
Step 5: Customize for Industry-Specific Needs
Different industries require different approaches to CRM and data security. Healthcare CRM software development needs to follow and comply with HIPAA and GDPR standards, whereas financial CRMs align with PCI DSS systems. Ensure that you hire AI developers from a dedicated CRM development company that has developers with industry expertise and specializes in implementing data security in CRM systems.
Step 6: Enhance Security with AI Workflow Automation
Effective CRM security relies on intelligent monitoring. AI workflow automation can identify unusual activity, predict potential threats, and improve governance rules. It is quicker and accurate than manual checks.
Step 7: Build a Human-Centred Security Culture
Awareness is the final step of securing CRM systems. Train employees for threats such as cybercrime, phishing, CRM data protection, and incident response processes. Look at the team as an integral part of the data protection act and CRM systems.
Key Data Protection Regulations for CRM Compliance
| Regulation | Region / Applicability | Key Requirements for CRM Data |
| General Data Protection Regulation (GDPR) | European Union | Explicit consent for data collection, right to access/erase data, breach reporting, privacy by design. |
| California Consumer Privacy Act (CCPA) | California, USA | Consumer rights to access, delete, and opt out of data sale; clear privacy policies; respond to consumer requests. |
| Health Insurance Portability and Accountability Act (HIPAA) | USA (Healthcare) | Secure storage, transmission, and access control of health-related data in CRMs. |
| Payment Card Industry Data Security Standard (PCI DSS) | Global (Payment card handling) | Secure handling of payment card information; encryption, access control, monitoring. |
| Sarbanes-Oxley Act (SOX) | USA (Public companies) | Secure retention and accurate record-keeping for financial data within CRM systems. |
| Children’s Online Privacy Protection Act (COPPA) | USA | Verifiable parental consent for collecting personal information of children under 13. |
| ePrivacy Directive (EU Cookie Law) | European Union | Consent for cookies and online tracking; privacy notices for behavior tracking in CRMs. |
| Personal Data Protection Acts (PDPA) | Various countries (e.g., Singapore, India, Malaysia) | Collect, store, and process personal data with explicit consent and purpose limitation. |
How Secure CRM Improves Business Operations
Improved Customer Trust: Consumers can share accurate data when they know their information is handled with care and respect. Security always builds confidence, which in turn fosters deeper relationships with customers, ultimately leading to improved retention rates.
Operational Continuity: Breaches and ransomware can cause downtime in CRM systems, which can make vital business functions cripple. In the implementation of Enterprise CRM solutions, it is important to incorporate fail-safe measures to ensure systems remain available, enabling teams to serve customers without interruption.
Data Accuracy and Reliability: By reducing unauthorized access and minimizing tampering risks, secure CRM maintains the integrity of data. Accurate information leads to better decision-making and a higher level of personalization.
Regulatory Advantage: Businesses that prioritize GDPR, HIPAA, and CCPA not only save themselves from severe penalties but also position themselves as reliable and trusted partners where compliance assurance is critical.
Scalable Growth: A secure foundation lays the groundwork for businesses to scale and extend CRM integrations, adapt AI-driven workflows, and manage larger datasets without compromising system security.
Why Hire Dedicated CRM Developers from CMARIX?
CMARIX is a highly dependable security software development firm. We possess the ideal combination of experience, security-driven development best practices, and expertise in creating CRM software tailored to your unique requirements.
What makes CMARIX stand out as a Reliable CRM Development Company
- CRM Expertise and Integration: We specialize in major CRM platforms like Salesforce and Microsoft Dynamics. We also design and build custom CRM systems from scratch to fit your specific business processes.
- Security and Compliance: We prioritize security from the start by using encryption and role-based access controls. Our solutions are designed to comply with best data privacy laws, including GDPR, HIPAA, and CCPA.
- Proven Experience: We have proven experience and expertise in delivering reliable, enterprise-level CRM solutions to businesses worldwide.
Final Words
Now you understand why it is essential to optimize CRM and data, and how to achieve this. Provide compliance with all relevant regulations in the targeted industry, maintain system security, identify potential vulnerabilities, and optimize your CRM with the assistance of a reputable CRM development agency.
FAQs on CRM and Data Protection
Why Is Data Security So Important for CRM Systems?
CRMs hold sensitive customer data. This includes personal details and financial records. A data breach can result in major financial loss. It can also damage your reputation and lead to legal issues. Secure data builds trust. It also minimizes risks.
How Can Businesses Protect CRM Data From Breaches?
Businesses should use strong encryption. They should also use multi-factor authentication to provide an additional layer of security to CRM systems. Update security protocols often. Conduct regular security audits. Train employees on best practices. Monitor for any suspicious activity. This helps catch breaches early.
Is Cloud-Based CRM Safe for Sensitive Customer Data?
Yes, cloud CRMs can be safe. It depends on the provider’s security. Good providers use strong encryption. They also have secure data centers. They comply with privacy rules. Select a vendor that adheres to security best practices. Make sure they offer customizable privacy settings.
What Are the Best Practices for CRM Data Backup and Recovery?
Automate your data backups. Store them securely. Use an off-site or cloud location. Test your recovery plan often. This ensures you can restore data fast. You will be prepared for any emergency.
What Features Should a Secure CRM Have?
A secure CRM needs data encryption. This protects sensitive data and utilizes two-factor authentication (2FA) to verify users. Using RBAC limits who can access data. Audit trails are important, too. They track who accesses data. Automated backups are a must. They save data regularly. They also allow for easy restoration.







